History and Evolution of Zero Trust Security

While John Kindervag, a Forrester analyst, brought the term "Zero Trust" to prominence in 2010, the concept itself originated with Stephen Paul Marsh in 1994. Marsh, in his doctoral thesis, envisioned trust as a quantifiable concept applicable to IT systems, separate from human emotions and social constructs like morals and law.
In this article we are giving an overview of Zero Trust Security and the 7 Pillars of Zero Trust security given by US Department of Defense(DoD)
Emergence of Zero Trust Security
The concept of "Zero Trust" has become a cornerstone of modern cybersecurity. This approach, built on the principle of "never trust, always verify," stands in stark contrast to the traditional perimeter-based model where trust was granted once inside the network. But the emergence of Zero Trust wasn't a sudden invention. It's a story of evolving ideas, a response to changing threats, and the foresight of key individuals.
Fast forward to the late 2000s, the cybersecurity landscape was changing. The rise of cloud computing and mobile devices challenged the traditional perimeter-based model. Google, facing these challenges head-on, developed its "BeyondCorp" initiative. This initiative, focused on securing access regardless of location or device, laid the groundwork for a Zero Trust approach.
In 2010, John Kindervag, an analyst at Forrester Research, popularized the term "Zero Trust." Recognizing the potential of BeyondCorp, Kindervag used "Zero Trust" to describe a new security paradigm – one that assumed no entity, user, or device was inherently trustworthy. This clear and concise term resonated within the security community, propelling the concept into the mainstream.
However, the widespread adoption of Zero Trust was gradual. It wasn't until the rise of sophisticated cyberattacks and the ever-increasing reliance on cloud services that organizations truly began embracing this new approach. The need for granular access control, continuous verification, and a focus on least privilege became more critical than ever.
Today, Zero Trust is no longer a fringe concept but a recognized best practice. Major security frameworks incorporate Zero Trust principles, and organizations across industries are implementing Zero Trust architectures.
The emergence of Zero Trust is a testament to the ongoing evolution of cybersecurity. It's a story of continuous improvement, driven by the dedication of researchers, the foresight of industry leaders, and the ever-changing threat landscape. As technology continues to advance, so too will Zero Trust, adapting to new challenges and ensuring the security of our increasingly interconnected world.
How does Zero Trust Security work?
Zero Trust security operates on the principle of "never trust, always verify." This means it ditches the idea of a secure internal network perimeter and constantly verifies every user and device trying to access resources. Here's a breakdown of how it works:
Continuous Authentication and Authorization: Zero Trust doesn't grant automatic access based on location (inside the network) or past logins. Every attempt to access a resource requires strong authentication (multi-factor authentication is common) and authorization checks. This verifies the user's identity, device health, and permissions for that specific resource.
Least Privilege Access: Zero Trust follows the principle of least privilege. Users are only granted the minimum access level needed to perform their tasks. This limits the potential damage if an attacker gains access to a user's credentials.
Microsegmentation: Networks are segmented into smaller zones with specific access controls. This isolates resources and prevents attackers from easily moving laterally within the network even if they breach a single point.
Context-Aware Access Control: Zero Trust considers various factors when granting access, such as user location, device type, time of access, and application being accessed. This allows for more granular control and reduces the risk of unauthorized access.
Continuous Monitoring: Zero user or device is trusted indefinitely. Zero Trust systems constantly monitor user activity and device health for suspicious behavior. This allows for quick detection and response to potential threats.
7 Pillars of Zero Trust Security
The U.S. Department of Defense (DoD) recently issued a Zero Trust strategy and roadmap.
The Department of Defense (DoD) Zero Trust model stands out for its thorough examination of core security principles. It highlights the interconnectedness of these concepts and offers practical guidance on implementing Zero Trust technologies across an organization's infrastructure. Notably, the DoD model acknowledges the potential impact on operations and user adoption. This comprehensive approach serves as a valuable blueprint for other industries, even those less extensive than the DoD.
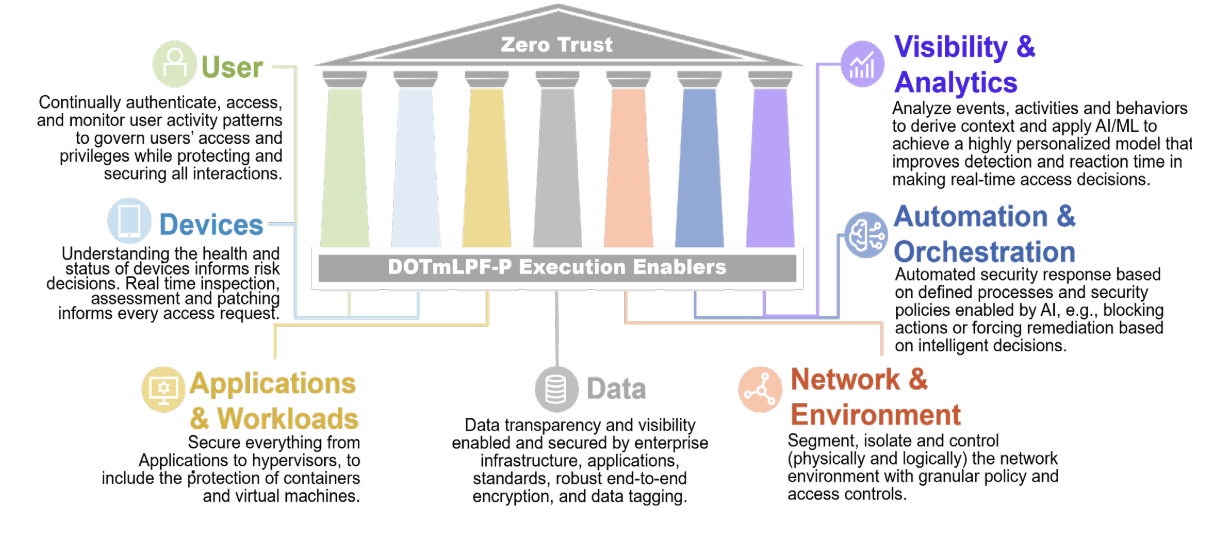
DoD Zero Trust Pillars
Identity and Access Management (IAM): Ensures strong authentication for all users and devices, including non-human entities like sensors. Access is granted only for specific sessions based on the user, access method, and resources used. Permissions are assigned for the minimum necessary access, and all user activity is monitored in real-time. End-to-end encryption adds an extra layer of security.
Endpoint Security: Focuses on securing all devices that can access the network, including user devices, servers, networks, and storage systems. Every device needs to be identified and authorized. Automated asset management ensures devices are updated with the latest patches and security protocols. Endpoint security solutions like UEM/MDM and EDR/XDR provide further protection.
Application and Workload Security: Secures applications and their operating environments, regardless of whether they're physical or virtual. It involves protecting hypervisors, containers, and virtual machines in both cloud and on-premises settings. Security extends beyond runtime to ensure secure development and integration practices throughout the application lifecycle.
Data Security: Focuses on protecting data at rest and in transit. End-to-end encryption is crucial for data transfer and storage on any device. Data classification and labeling allow for granular access control, monitoring, rights management, and loss prevention.
Network Segmentation: Focuses on dividing and managing the network infrastructure into smaller, isolated zones (micro-segmentation) instead of relying on traditional macro-segmentation (e.g., VPNs) that grants access to all resources. Software-Defined Networking (SDN) provides flexibility and programmability to achieve micro-segmentation.
Automation and Orchestration: Recognizes the importance of automation for efficient access control and security response. Using tools like domain controllers for device and network management, automated processes ensure timely patching, encryption, and blocking of suspicious activities based on AI/ML analysis. This requires seamless integration between existing IT management tools like SIEMs, SOARs, and element managers.
Visibility and Analytics: Ensures comprehensive network visibility for IT teams. It allows them to monitor all events, activities, and user behavior, leveraging AI/ML for deeper insights and faster response times. This involves activities like logging network traffic, analyzing user and entity behavior, collecting and evaluating events and alerts, and incorporating threat intelligence from external sources.
Zero Trust security in 2024
Over the past decade, Zero Trust has undergone a remarkable transformation. Once a fringe security concept, it's now a widely adopted approach for securing organizations worldwide.
The future of Zero Trust is bright, with continual adoption expected. Unlike a single product, Zero Trust is a philosophy. Many organizations unknowingly implement measures that align with these principles, potentially being further along the path than they realize.
Security experts acknowledge room for improvement in Zero Trust implementation across various sectors. This requires advancements in both security policies and technology tools, along with refinement of deployment and user practices.
Federal government influence has spurred the adoption of "verify then trust" principles in entities like state and local governments, universities, and critical infrastructure companies.
To accelerate Zero Trust adoption, analyst firms and organizations have developed implementation roadmaps. These roadmaps offer step-by-step guidance for organizations to assess their current Zero Trust maturity and establish a comprehensive "verify then trust" security posture.
Recommended Posts

In today's knowledge-driven economy, intellectual property (IP) plays a pivotal role. However intellectual property disputes lead to complex legal battles
Read More

Learn how to recognize the signs of a computer hack and implement preventative measures to secure your sensitive information.
Read More

Privacy, once a concept centered around physical space and control over personal information, has undergone a dramatic transformation in the digital age.
