

Explore the top security risks in open source software, including vulnerabilities, malicious code, and dependency issues. Learn how to mitigate these threats.

Secure file transfer(SFT) is a method of sharing data that employs encryption and secure protocols to protect information during transmission. Unlike traditional file sharing methods that leave data vulnerable to interception, SFT ensures that sensitive files remain confidential.

Ever imagine being locked out of your own data? That's the chilling reality of a ransomware attack..

In this article we are giving an overview of Zero Trust Security and the 7 Pillars of Zero Trust security given by US Department of Defense(DoD).

In today's knowledge-driven economy, intellectual property (IP) plays a pivotal role. However intellectual property disputes lead to complex legal battles

The internet, a vast digital landscape brimming with opportunities, has unfortunately become a breeding ground for a malicious practice: brand abuse.

Supply chain attacks are cyberattacks that target the weak links in an organization's supply chain, rather than going after the organization itself.
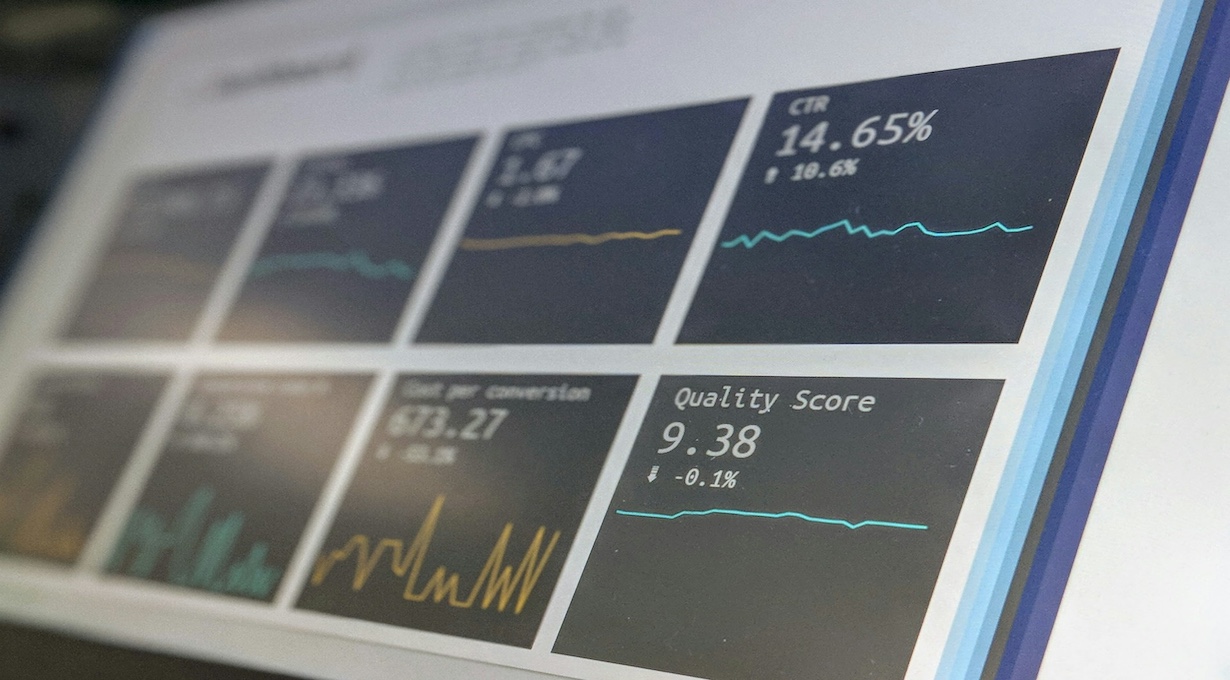
Organizations are accumulating vast amounts of data within their IT infrastructures and need data loss prevention strategies to protect their valuable information.

Learn how to recognize the signs of a computer hack and implement preventative measures to secure your sensitive information.

Malware, short for malicious software, a term encompassing malicious software, has been a persistent threat since the dawn of the digital age.

How to Detect Phishing Attacks. Learn top 10 tips to spot phishing emails and protect yourself from online scams.

From mobile banking to online shopping, from healthcare systems to smart devices, software applications facilitate communication and enhance productivity.

Avoid using the same password for multiple accounts. The longer the password, the harder it is to crack. Aim for at least 12 characters.

Mobile devices have become an indispensable part of our lives. From communication to banking, these pocket-sized powerhouses hold a wealth of information.

Privacy, once a concept centered around physical space and control over personal information, has undergone a dramatic transformation in the digital age.